Table of Contents
What is a Stresser?
By simulating large traffic volumes, stressers aid in preventive cybersecurity.
Exploring Booter Services

Booter services are essential for organizations testing load limits.
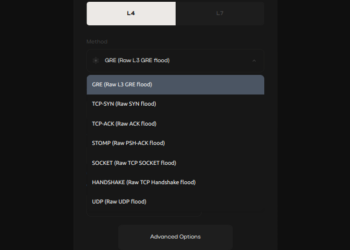
IP Spoofing and Layer 4 Attacks
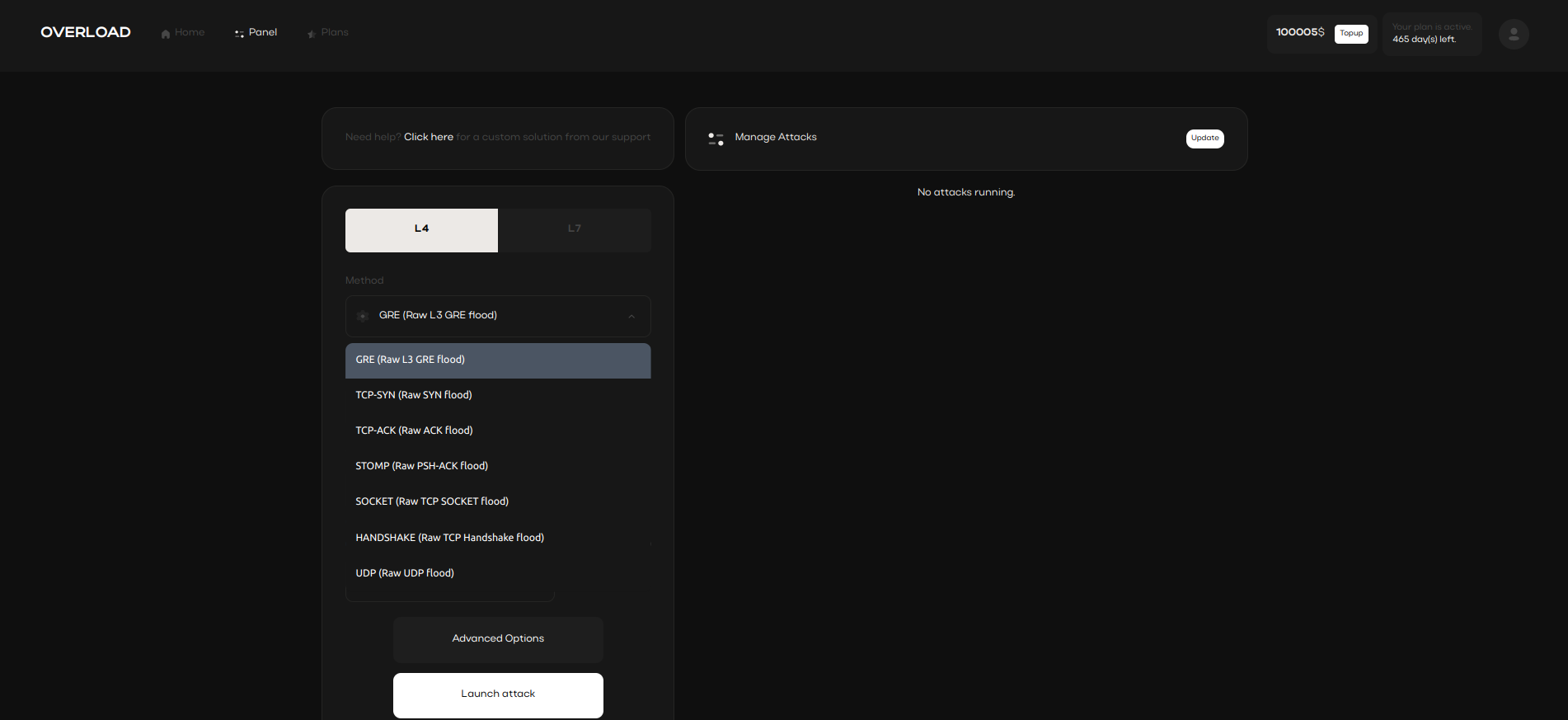
IP spoofing techniques in Layer 4 attacks help conceal attack sources.
Amplification Methods in Stresser Services

CLDAP, DNS, and NTP amplify network requests, stressing system capacities.
- DNS reflection method
- NTP amplification
- CLDAP amplification